This week exercises are based on password attacks. Exercises in this post are from terokarvinen.com.
a)
First task was to crack password hashes. First I needed to find hashes to crack, so I installed one box from vulnhub, which had tag “password cracking”. I started to break into the box so I could try out cracking the passwords.
I had to find the IP address of the box first and I used a tool called netdiscover for that.

Then I used nmap -A to scan the host. -A flag does OS and service scan in addition to port scan.

Nmap revealed two open ports: 80 and 22. So there is a webserver running on the host. Let’s run a tool called Dirb against it, to check if it finds some interesting hidden subdomains.

I ran a tool called Wpscan against my target, and it revealed some useful information.

I tried various metasploit exploits against it but with no luck. In this part I had to cheat a little bit and read a part of the walkthrough I found.

This plugin was the only thing I hadn’t try yet, and it had the vulnerability I was able to exploit.
I searched searchploit for that plugin name and found this:

After finding this I navigated back to the wordpress site on the webserver and pasted the path show on above screenshot and was able to display the /etc/passwd file which had a password hash.

First password hash found! Now it’s time to crack it. I used a tool called hashcat to crack the first password. I copied the md5crypt hash to a text file and typed the following:

I am using a prebuild wordlist rockyou.txt which is found from Kali by default. It took hashcat 14 seconds to crack this hash. Hashcat is able to utilize the GPU processing power to crack hashes. It wasn’t using my GPU though, probably because it was VM and no graphics drivers installed.
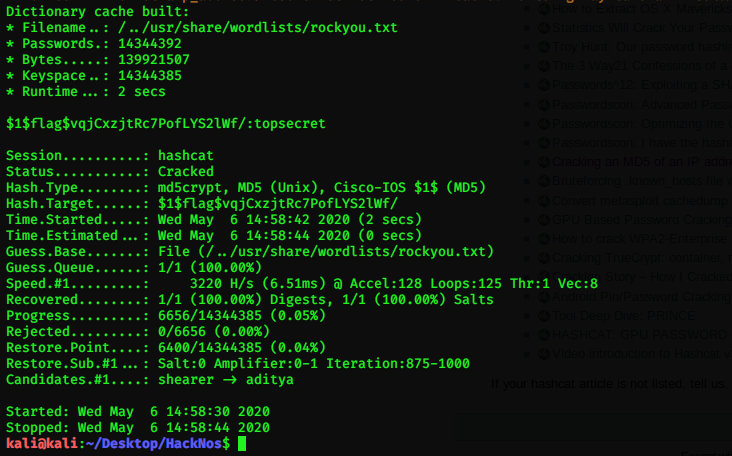
Now I had one username and one cracked password. First I tried to log in to wordpress admin page, but had no luck there. I thought let’s try ssh then.

I was able to log in remotely to the target box by using ssh. After some browsing on the remote host, I found another password hash:

Maybe I should try another password cracking tool this time. Let’s give John a try.

I used the rockyou.txt wordlist again and it took nearly two minutes to crack the hash successfully. The password was more complex than the first one so probably that’s why it took a little bit longer, although two minutes is not long.
Logging in to the remote box using ssh and the lastly cracked password with username “rohit” gave root access. There was one more raw md5 hash which I wasn’t able to crack yet. Wonder what’s that for.

b)
Second task was to try brute force credentials using online attack. This is where a tool named Hydra will come in handy. First I tried brute forcing metasploitable dvwa login but with no success:

I think I had incorrect syntax in the post part, because hydra stated that it found 90 correct passwords. It seems that it successfully used the wordlist and passlist but in incorrect way.
Then I tried using it to brute force metasploitable ssh credentials and was succesful with that:

I tried it first with wordlist and it didn’t find any credentials, even though I added the correct login information for testing. Maybe it was because I didn’t use the -t flag.
I tried with correct login and password and it was successful. Then I tried again with the wordlists but using the -t flag this time, and it was able to brute force the ssh login.
c)
This task was focusing on lateral movement and collecting the password hashes from hosts. I used metasploitable2 as a target and used metasploit hashdump module against it.
I began this task by creating a new workspace in metasploit and scanning my target to list the open ports:

Now I have a workspace dedicated to metasploitable2 which has information of the open ports:

Then I decided to use the vsftpd exploit which gives me a shell on the remote machine. After getting a shell, I put the session to run on the background so I can set the post exploitation module hashdump:

Now I can use the session on the background which has a shell and tell hashdump module to use that. When the options has been set and after running the exploit, I was succesful with extracting some password hashes from the remote machine!


After getting the password hashfiles I started cracking them with John. It seems that John has a lot easier syntax than hashcat – I didn’t have to specify hashtypes or wordlist path, because John has it own. Because the passwords were not complex and every wordlist contains them, cracking them wasn’t a hard task.

d)
This task’s goal was to investigate the source code of the infamous DDoS botnet Mirai, and find the attack part of it. The source code was leaked to public in 2016 probably by the author of Mirai. It can be found from here.
This task was interesting but hard, as I’m not familiar with C programming language, and I’m not sure if my analysis is correct. I read this article and used it as reference to better understand Mirai’s functionality.
There are many interesting functionalities in Mirai, including scan for other malware, blocking up several IP address ranges and prebuilt username and password lists for default credentials used by IoT devices. Mirai is capable of launching attacks using at least following protocols: UDP, TCP and HTTP. There were own .c files for each of the protocols at github. Screenshot below is from attack_tcp.c file.

There was a lot of mentions of IP addresses above this part of the code, and I assume it was to configure the attack. The screenshot above is from the end of that code file, and has a comment “Start spewing out traffic” so it seems this might be the part where the attack happens.
There were two more tasks: try some other password cracking/dumping technique and solve more webgoat exercises. Unfortunately I’m running out of time and I have to come back and finish these two tasks later.
References:
https://medium.com/hacker-toolbelt/metasploitable-2-ii-port-21-470ee8639278
https://www.simonroses.com/2016/10/mirai-ddos-botnet-source-code-binary-analysis/
https://www.hacknos.com/os-hacknos-2-walkthrough/
